Policy as code (PaC) is a concept that treats infrastructure policies, configurations, and security rules as code artifacts. This approach allows organizations to define, manage, and enforce their policies using the same version control, testing, and continuous integration practices they apply to their software code.
Managing cookbook dependencies, setting up environments, and giving nodes roles are crucial duties in the realm of Chef Infra. Traditionally, these tasks have been handled separately, requiring multiple artifacts and intricate workflows. However, the introduction of Policyfiles has completely transformed Chef cookbook management.
Policyfile.rb
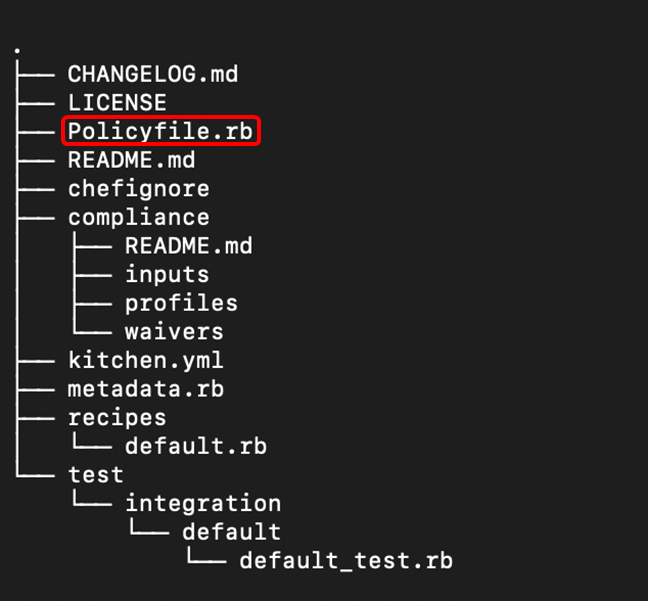
To understand the policyfile.rb file, let us take a closer look at its syntax:
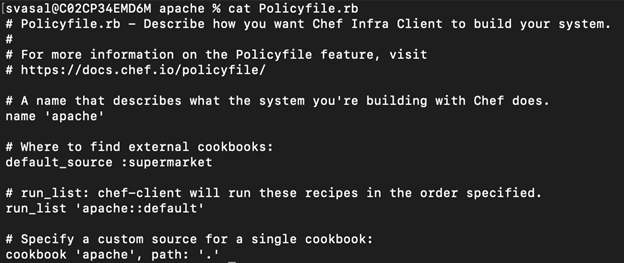
Above is an instance of the Policyfile that was automatically generated when the command $ chef generate cookbook apache was executed.
- name: This field serves not only as a label for the Policyfile but also replaces the traditional role object. Choose a name that accurately represents the intended function of the systems where the policy will be implemented.
- default_source: Indicates the location from which cookbooks are retrieved when they are not explicitly declared in the "cookbook" section. Typically, this refers to a public or private supermarket or the Chef Infra Server. Additionally, default_source can be utilized for an internal repository housing all the organization's cookbooks.
- run_list: This sets the run list for any nodes using this Policyfile. Run lists are an ordered list of roles and/or recipes that are run in the exact order defined in the run-list; if a recipe appears more than once in the run-list, Chef Infra Client will not run it twice.
- cookbook `<name>`, path: declares the non-default location where cookbooks can be found.
Follow along these steps to generate a policyfile:
We shall first generate a policyfile for apache, including a run list followed by generating a policyfile.lock.json file. After which we shall push the lock.json file to the Chef Infra server and apply the policyfile to a node.
- In your chef repo, create a separate directory for your policyfiles
$ mkdir policyfiles
- Use the command to generate a file
apache.rb
$ chef generate policyfile apache - Using the
cat apache.rbcommand, view and modify the policyfile if required and add the path to the apache cookbook.
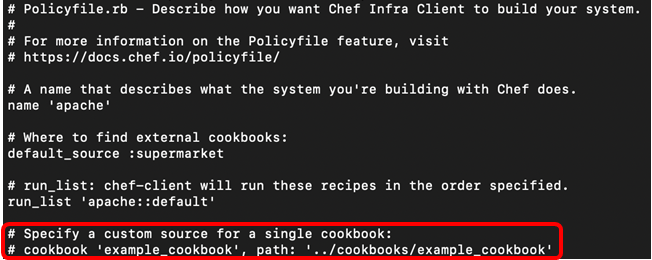
Policyfile.lock.json
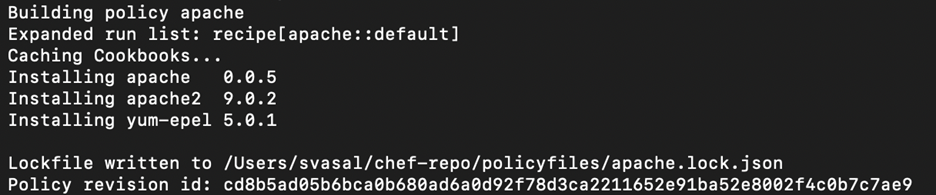
Now that we have our Policyfile.rb(apache.rb) we need to generate the Policyfile.lock.json(apache.lock.json)
$ chef install <policy_name> command creates the Policyfile.lock.json. policy_name with apache.rb - The versions of cookbooks in use
- A hash of cookbook content
- The source for all cookbooks
- Attributes included with the Policyfile
This file is associated with a revision_id , which is a unique hash that is used to identify versions of the particular policyfile. A new revision_id is generated every time the file is updated or modified.
![]()
Policy Groups
Pushing a policyfile to Chef Infra Server
- The first time you specify a policy group, that policy group name will be instantiated in Chef Infra Server. For instance, Running the command:
$ chef push prod apache.lock.json Will create the policy group named prod and upload the apache.lock.json to the Chef Infra Server.
- Run the command
$ chef show-policyto confirm that the policy is on the Chef infra server.
- Use the
$ knife node policy setcommand to apply the policyfile to a node.
$ knife node policy set apache_web prod apache
- Now, run the command to connect the linux node with ssh
$ knife ssh IPADDRESS –m -x chef -P PWD 'sudo chef-client'

