
Chef Cloud Security
End-to-End Cloud Security and Compliance Management Software
Prevent security incidents and maintain compliance across your cloud native assets.
Gain Visibility and Limit the Risk of Misconfigurations
Chef® Cloud Security™ makes it possible for you to scan, monitor, and remediate configuration issues in your multi cloud accounts, across on-prem and cloud native environments. It is easier than ever to maintain and enforce compliance with standards based audit. You can tune baselines to adapt to the organization’s requirements, maintain visibility and control across hybrid environments.
Chef Cloud Security
Gain Visibility Through Streamlined Audits
Chef Cloud Security audits your cloud accounts for security risks and misconfigurations across hundreds of configuration settings and enables consistent, unified multi-cloud security.
Maintain Continuous Compliance
Close the loop between audit and remediation to ensure assets are always in compliance with CIS benchmarks.
CSPM and Cloud-Native Security
Chef Cloud Security can help you scan systems across all environments (Dev, Pre-Prod, Prod), all systems (Cloud, Kubernetes, VMs, Containers, Windows, Linux), and all clouds (AWS (Amazon Web Services), Azure, Google, Alibaba, and many others).
Coded Approach
Code is at the center of all our solutions and Chef is leading the evolution from “Infrastructure as Code” to “Policy as Code” which merges infrastructure, security, and compliance concerns into a single framework.
Jump Start Compliance Automation Efforts with Chef Premium Content
Customers access Chef curated trusted content for audit that is directly aligned to CIS (Center for Internet Security) benchmarks or DISA Security Technical Implementation Guides.
Chef Premium Content now offers new cloud target scanning that allows users to easily scan an extensive set of cloud resources across all major public cloud providers, as well as container and Kubernetes deployments.
| Environment | Audit |
|---|---|
| CIS Amazon Web Services Foundation Benchmark - Level 1 & 2 | ● |
| CIS Azure Foundations Benchmark - Level 1 & 2 | ● |
| CIS Docker Community Edition Benchmark - Level 1 & 2 | ● |
| CIS Kubernetes Benchmark 1.6.1 - Level 1 & 2 | ● |
| CIS Google Kubernetes Engine | ● |
| CIS Redhat OpenShift Container Platform | ● |
Infrastructure-as-Code Template Scanning
Check Terraform templates for security issues before your applications are deployed. Applying “shift left” security reduces your risk and security incidents in production.
Learn more about Infrastructure-as-Code Template Scanning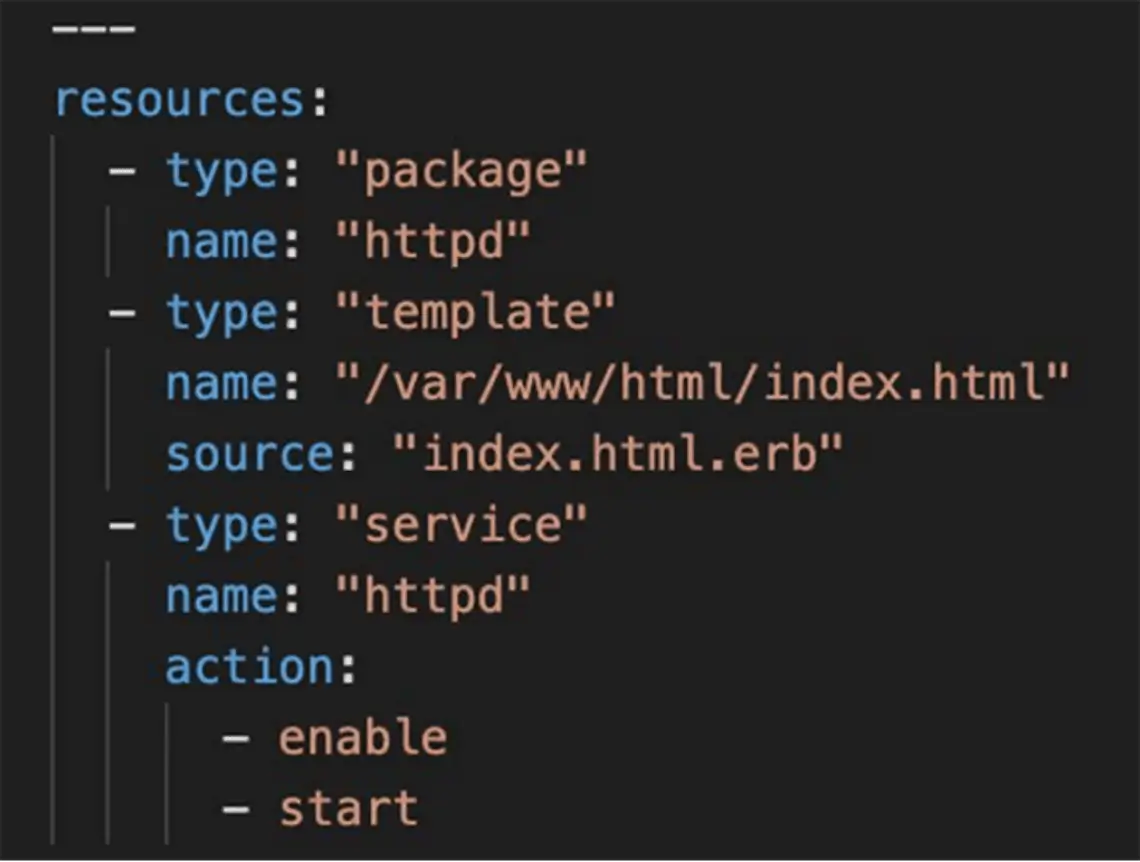
Continuous Compliance Audit
Chef Cloud Security comes with extensive audit content based on CIS benchmarks out of the box that can be easily tuned to meet specific needs of every organization to evaluate the security of your cloud accounts and ensure compliance.
Learn more about Continuous Compliance Audit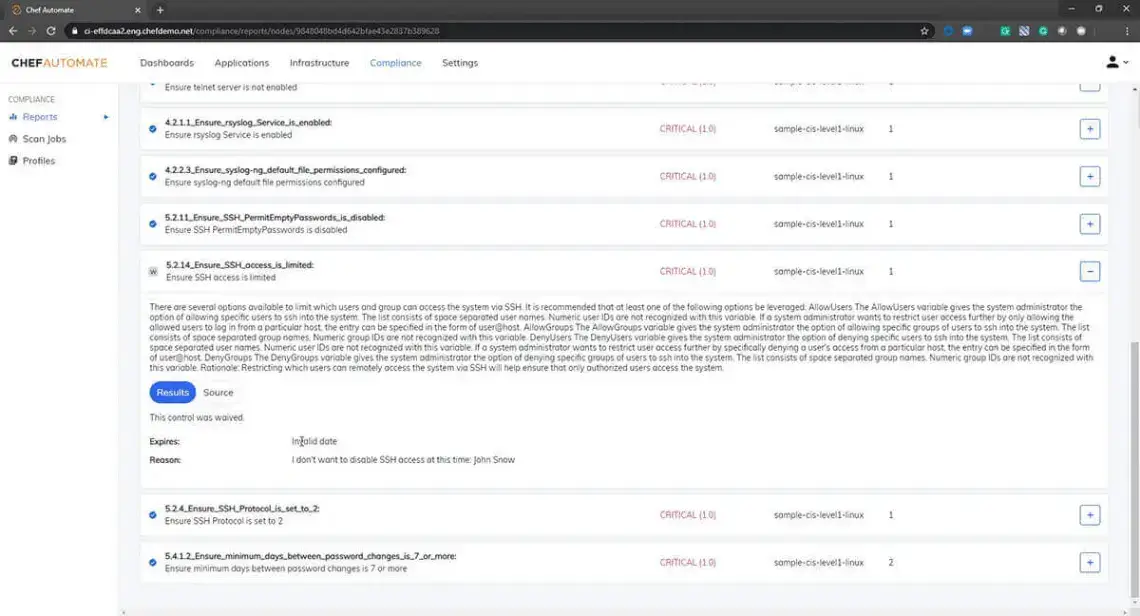
Policy as Code
Policy as Code enables DevSecOps automation with the use of a common pipeline and framework to implement configuration changes while simultaneously maintaining compliance. With Chef’s Policy as Code approach, configuration management is consistent and more efficient, and it also increases release velocity.
Learn more about Policy as Code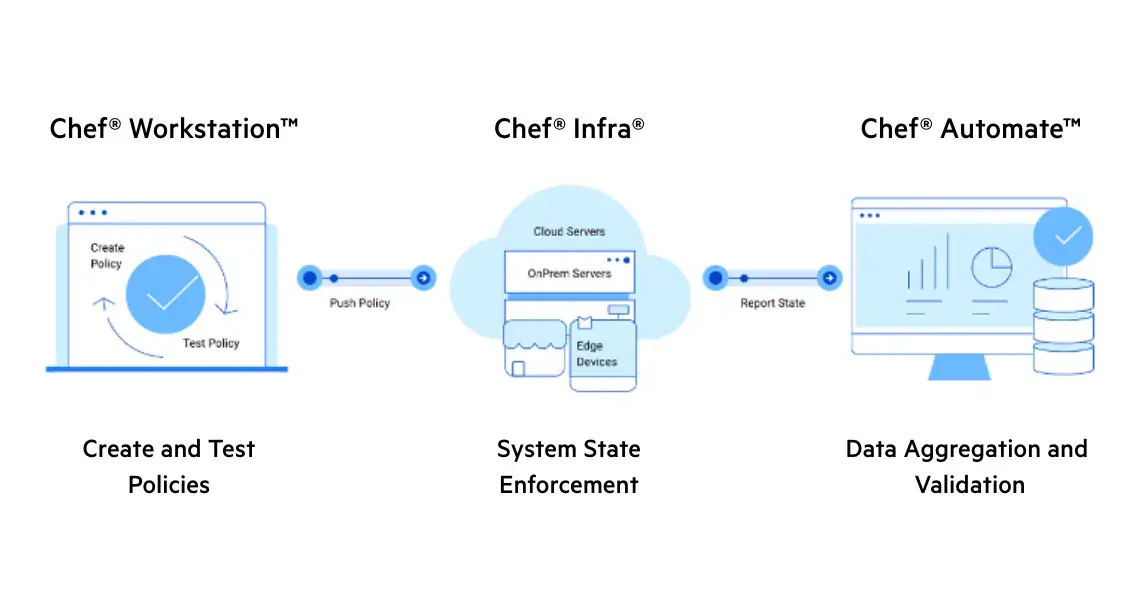
Level Up Cloud Security With Chef
Custom Profiles Tuned to Organization Needs
Chef Cloud Security also has the extensibility and flexibility to allow for customization of pre-packaged audit content that can be modified to accommodate for corporate specific needs through code. It also gives plethora of InSpec cloud resources which can be leveraged to codify custom profiles according to the needs of organisation.
Visibility
Chef Cloud Security enables security and operations teams maintain complete visibility over the compliance status for public clouds. Achieve Security Automation to detect and correct security issues before they go into production to reduce risk, increase speed, and improve efficiency.
Enterprise Scale
Support for multiple users and teams with SSO using SAML 2.0 and LDAP/Active Directory. Chef Cloud Security integrates with Incident Management tools such as Service Now collaboration tools, including Splunk, Slack, analytics, and monitoring tools. Fully documented RESTful APIs make it easy, for you to create additional integrations and automate workflows.
Community Support
The Chef community is known for the value they bring to the product. You can access user contributed content and resources to help you get started. The community offers constant support for all Chef products and enables collaboration bringing together innovation from different development teams.
Become a part of the Chef Community SlackChef Cloud Security Use Cases
Secure Hybrid Cloud Management:
Manage both cloud and on-prem environments (Cloud Instances, VMs, Multi-Tier Apps, Jenkins, Azure DevOps, GitHub) using the same tools and processes
Multi-Cloud:
Continuously audit cloud accounts and services for security risks and misconfigurations. Achieve consistent security across AWS, Azure, Google, and Alibaba Cloud
Cloud-Native CI/CD Pipeline Governance:
End-to-end Cloud Native environment configuration and security validation (AWS, Azure, Google), scan live running containers, and Validate K8 settings
Audit for Compliance:
Automate CIS benchmark tests for Cloud Fundamentals, Kubernetes, and Docker

Cloud Security Customer Success Story

SAP: Taking Control with CSPM and Chef InSpec for the Public Cloud
Chef provides SAP with a highly flexible tool to manage the compliance of their cloud accounts. It allows teams using public cloud to “shift-left” and adopt DevSecOps practices for public cloud infrastructure, as well as verify the status of their cloud accounts whenever they want. SAP runs a fully private Chef InSpec Kubernetes cluster of three nodes that scanned the entire landscape (around 8 million cloud resources) in three hours while taking over 900 exceptions (or waivers).
Read the customer story here.Chef Clients Solves Top 3 Use Cases
Overcome Technical Skill Gaps
With hundreds of out-of-the box resources and helpers, automated waivers, built-in testing tools, CIS/DIS STIG aligned profiles, Visual UI, and free online learning, Chef Client provides the tools and resources to eliminate technical skill gaps. Our community of users provide a direct connection with our Chef team, other developers and even more DevRel resources to help you become an expert.
Optimize ROI with Adoption
Key Performance Indicators are ingrained in every successful organization to determine the profitability of an expenditure. With an investment in Chef Client, use the same tool and language for all systems and environments, a fully extensible language for both hybrid and multi cloud support. The robust enterprise management platform offers rich APIs, and data feeds that integrate with corporate BI/AI systems with codified articles to automate workflows and pipeline.
Limit Risk and Increase Speed
Shift left policies and checks run at every stage of the pipeline with enterprise-wide control and visibility. Limit your organization’s risks with hardened systems that slow down non-necessary processes and our codified artifacts feed automated pipelines with functional testing that ensure what you ‘fix’ then ’works’.

Whitepaper
Building Security Resilience in the Cloud with Cloud Security Posture Management
Download Now On-Demand
On-Demand
Webinar
Secure your Cloud Infrastructure with Kubernetes Security Posture Management (KSPM)
RegisterFrequently Asked Questions
What is cloud security management?
Cloud security management involves applying strategies and deploying security tools to help keep cloud applications, services, data and development projects safe from threats and vpnerabilities. On the strategy side, cloud security management involves policies, best practices and governance. Cloud security tools help safeguard everything from end-user application data to internal IT infrastructure interacting with the cloud.
What are the categories of cloud security?
There are myriad cloud security categories. Here are the types of protection:
- Access Management: Controls who can get to data and services.
- Encryption: Blocks hackers from using data they find.
- Privilege Management: Defines what users can or can’t access.
- Authentication: Makes users prove who they are.
- Disaster Recovery: Restores data that was compromised.
- Compliance: Adherence to regulations and legal and contractual obligations.
- Cloud Security Posture Management (CSPM): Manage security posture by discovering, blocking and responding to risk in cloud infrastructure.
- Data Loss Prevention (DLP): Stopping data theft and leakage from outsiders and insiders.
- Privacy: Keeping personal data away from those with no right to access it.
- Cloud Visibility: Provides insight into cloud infrastructure.
- Workload Security: Protects workloads including virtual and container-based workloads.
- Vulnerability Management: Discover and close vulnerabilities.
What are the top security issues in cloud computing?
IT needs to understand what they are responsible for, versus what the cloud provider is responsible for. Under the Shared Responsibility Model, cloud providers protect their offerings, including:
- Physical Security
- Host Infrastructure
- Network Controls
For PaaS and SaaS solutions, providers also help protect:
- Application-Level Controls
- Identity and Access Management
- Client and Endpoint Protection
These three are shared responsibilities between providers and IT.
Top cloud security issues include:
- Misconfiguration
- Lack of visibility across all aspects of cloud infrastructure
- Data breaches
- Shortcomings in access control or unauthorized access
- Unsecured APIs and services
- Failures in security and compliance auditing
What are the types of cloud security solutions?
Here are five of the top areas:
Cloud Security Posture Management (CSPM): This requires security and compliance management products to help IT create and maintain a secure cloud infrastructure environment free from vulnerabilities and misconfigurations.
Incident detection, response and remediation: Incident detection and response applications can help secure your cloud environment, discovering threats and providing root cause analysis.
Additionally, hosting incident detection, response and remediation in the cloud can help provide greater security for on-premises and cloud-based assets. IT stakeholders, such as admins and security professionals, all have the same view of what is happening across the monitored cloud environment.
Cloud-based backup and recovery: On-premises storage hardware, software and networking components are immensely complex and have difficulty scaling to securely keep up with data storage needs that multiply over the years. Cloud backup, recovery, disaster recovery and business continuity store and protect data without IT having to manage and grow disk arrays, storage area networks and update the software that keeps it all.
Cloud backups for on-premises data systems help protect data from threats such as ransomware attacks.
Cloud security audits: Companies that face compliance challenges or that just want a clear record of security, rely on solutions such as Progress Chef to audit cloud accounts and discover and track security risks, such as misconfigurations.
Continuous compliance: Compliance is best done as a regular process. Even better as a continuous one. Continuous compliance closes the loop between audit and remediation, letting IT know their infrastructure assets are constantly in compliance with security frameworks such as CIS benchmarks.
What are the biggest threats to security in the cloud?
There are countless cloud threats and new ones appear with alarming regularity. Not all threats are from the outside; some are organizational.
Not enough cloud security expertise: The rate of cloud changes creates new attack surfaces, making it tough for even the best pros to keep up.
Poor cloud visibility: The cloud, and now the move to having hybrid clouds and multi-cloud, presents a huge visibility challenge.
Account takeover attacks: Access and identity attacks, which often lead to escalation of privilege attacks, are one of the biggest cloud security risks.
Other issues include:
- Insecure coding
- Excess permissions
- Poor or poorly configured communication protocols
Here are a few more areas of cloud vulnerability:
- Misconfiguration
- Compliance risks and violations of compliance policies
- Employees not following compliance regulations
- Poor alerting and notification of security and compliance issues
- Denial-of-Service (DoS) attacks
- Data loss and leakage from hacks
- Vulnerable access control points
What are the main benefits of cloud security management?
Here are 12 benefits of cloud security management:
- Maintained compliance
- Improved information privacy
- Tighter access control
- Increase cloud visibility
- Threat mitigation
- Advanced threat detection
- DDoS protection
- Data encryption
- Data recovery
- Fewer misconfigurations
- Better cloud availability
- Improved Access Management
How does Chef Cloud Security help your cloud security management?
Progress Chef® Cloud Security™ makes it possible for you to scan, monitor and remediate configuration issues in your multi-cloud accounts, across on-premises and cloud-native environments. It is easier than ever to maintain and enforce compliance with standards-based audit. You can tune baselines to adapt to the organization’s requirements, maintain visibility and control across hybrid environments.
Chef Cloud Security can:
- Runs regular audit scans across all cloud infrastructure including containers
- Supports key security benchmarks and controls such as SOC2 and PCI DSS
- Helps with creating and implementing compliance policies
- Discovers issues and guides remediation
- Discovers misconfigurations
- Measures security and compliance postures
- Enforces compliance for cloud assets
- Tracks metric and KPIs via trend and historical views